
In today's world, security is a crucial aspect of our day-to-day life, whether it's protecting personal information, financial transactions, or confidential company data. This has led to the development of various encryption algorithms, including the Rijndael algorithm, which has gained widespread popularity. Developed by Belgian cryptographers, the Rijndael algorithm is a symmetric key block cipher, which is used to secure data by converting it into an unintelligible form.
In search of a more robust and efficient encryption standard to replace triple DES, the US government launched a competition that drew in submissions from cryptographic experts worldwide. Vincent Rijmen and Joan Daemen, two Belgian cryptologists, submitted Rijndael, which impressed the evaluators with its superior performance, ease of implementation on both hardware and software, and top-notch security features. As a result, Rijndael was chosen as the Advanced Encryption Standard for the United States, quickly gaining popularity and becoming the go-to encryption standard worldwide.
One common use case of the Rijndael algorithm is in secure file transfer. For instance, a company needs to send a sensitive file containing confidential data to a client or business partner. They can use the Rijndael algorithm to encrypt the file before sending it. The sender encrypts the file with a secret key that is only known to them and the recipient. When the recipient receives the encrypted file, they use the same secret key to decrypt it, making it readable again. This use case of the Rijndael algorithm ensures that the sensitive information in the file is protected from unauthorized access during transfer. It is especially critical in industries such as finance, healthcare, and government, where confidential data needs to be securely transmitted over networks or stored in databases. The Rijndael algorithm's high level of security, efficiency, and flexibility makes it a popular choice for secure file transfer and other data encryption applications.
How does the Rijndael Algorithm work?
The Rijndael algorithm is a symmetric key block cipher, which means that the same key is used for both encryption and decryption, and it operates on fixed-size blocks of data. The size of the block and the key can vary, but the most common size is 128 bits. The Rijndael algorithm follows a series of steps to encrypt or decrypt the data, which are as follows:
Key Expansion:
A) Key Schedule: The key schedule algorithm for the Rijndael algorithm begins by taking the original secret key and arranging it in a specific pattern called the key matrix. The key matrix is a rectangular array of bytes with dimensions determined by the block size and key size. For example, for a 128-bit key and a 128-bit block size, the key matrix is a 4x4 array of bytes.
B) Key Expansion: The key expansion in the Rijndael algorithm is a crucial step that transforms the secret key into a set of subkeys, which are used in the subsequent rounds of the encryption or decryption process. The key expansion process generates a larger number of subkeys from the original key, providing enhanced security against various cryptanalysis techniques.
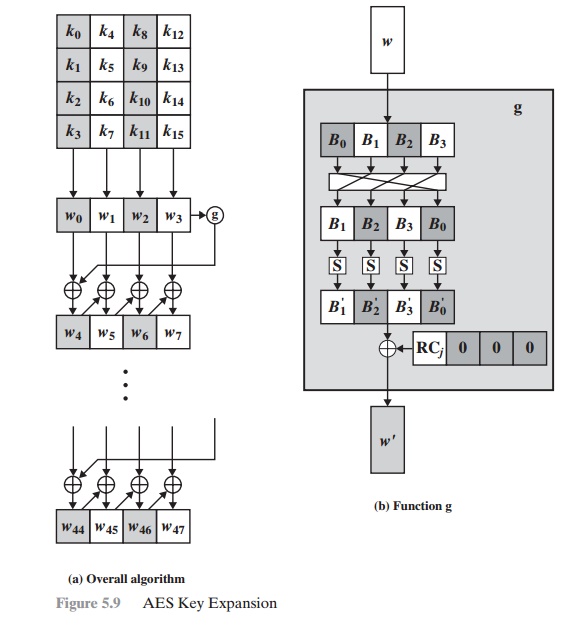
The key expansion process is determined by the block size and key size of the Rijndael algorithm. The standard block size is 128 bits, while the key size can vary between 128, 192, and 256 bits. The key expansion process is slightly different for each of these key sizes. For the 128-bit key, the key expansion process generates ten rounds of subkeys. For the 192-bit key, the process generates twelve rounds of subkeys, while for the 256-bit key, it generates fourteen rounds of subkeys.
The key expansion process begins by taking the original secret key and arranging it in a specific pattern. The pattern depends on the key size, and it is arranged in a rectangular matrix called the key schedule. The key schedule is then used to generate a series of intermediate keys, which are XORed with each other to generate the final subkeys. The intermediate keys are generated using a key schedule algorithm that applies specific transformations to the previous intermediate key. The algorithm uses various S-boxes, which are fixed tables of values that provide confusion in the cipher. The algorithm also uses a fixed permutation matrix that provides diffusion in the cipher. The key expansion process generates a large number of subkeys, which are used to perform the AddRoundKey operation in each round of the Rijndael algorithm. The key expansion process provides added security against various cryptographic attacks, including brute-force attacks, differential cryptanalysis, and linear cryptanalysis.
Rounds:
The encryption or decryption process involves a series of rounds that are repeated a specific number of times, depending on the key size and the block size. Each round consists of four steps:
AddRoundKey: In the first round, the state is XORed with the first set of subkeys generated from the original secret key. This operation combines the state with the subkey and provides an additional level of security to the algorithm.
SubBytes: In this step, each byte in the state is substituted with a value from the S-box. The S-box is a fixed table of values that provide confusion in the cipher. The substitution is nonlinear and depends on the byte value, which adds an extra layer of complexity to the algorithm.

ShiftRows: In this step, the rows of the state are shifted by a fixed number of bytes. The first row remains unchanged, while the second, third, and fourth rows are shifted to the left by 1, 2, and 3 bytes, respectively. This operation provides diffusion in the cipher and ensures that each byte in the state affects the encryption of multiple bytes.
MixColumns: In this step, each column of the state is transformed using fixed matrix multiplication. The matrix multiplication involves a set of fixed coefficients and ensures that the byte values in each column are mixed. This operation provides additional diffusion in the cipher and enhances the security of the algorithm.

These four steps are repeated for a fixed number of rounds, depending on the block size and key size of the algorithm. The number of rounds ranges from 10 to 14 rounds for 128-bit to 256-bit keys. The last round of the encryption or decryption process does not include the MixColumns step.
The decryption process for the Rijndael algorithm involves the reverse steps of the encryption process, where the subkeys are used in reverse order. The decryption process includes the following steps:
AddRoundKey: The last set of subkeys is XORed with the state.
InvShiftRows: The rows of the state are shifted in the opposite direction of the ShiftRows step.
InvSubBytes: The bytes in the state are substituted with the inverse of the S-box.
InvMixColumns: The columns of the state are transformed using the inverse of the MixColumns matrix multiplication.
These steps are repeated in reverse order for a fixed number of rounds to obtain the original plaintext.
Following is a sample implementation of the Rijndael algorithm in Java for file transfer:
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.security.Key;
public class RijndaelFileTransfer {
private static final String ALGORITHM = "AES";
private static final String TRANSFORMATION = "AES";
public static void encrypt(String key, String inputFile, String outputFile) throws Exception {
doCrypto(Cipher.ENCRYPT_MODE, key, inputFile, outputFile);
}
public static void decrypt(String key, String inputFile, String outputFile) throws Exception {
doCrypto(Cipher.DECRYPT_MODE, key, inputFile, outputFile);
}
private static void doCrypto(int cipherMode, String key, String inputFile, String outputFile) throws Exception {
Key secretKey = new SecretKeySpec(key.getBytes(), ALGORITHM);
Cipher cipher = Cipher.getInstance(TRANSFORMATION);
cipher.init(cipherMode, secretKey);
FileInputStream inputStream = new FileInputStream(inputFile);
byte[] inputBytes = new byte[(int) inputStream.getChannel().size()];
inputStream.read(inputBytes);
byte[] outputBytes = cipher.doFinal(inputBytes);
FileOutputStream outputStream = new FileOutputStream(outputFile);
outputStream.write(outputBytes);
inputStream.close();
outputStream.close();
}
public static void main(String[] args) {
try {
String key = "sample_key";
String inputFile = "/path/to/input/file";
String encryptedFile = "/path/to/output/encrypted_file";
String decryptedFile = "/path/to/output/decrypted_file";
// Encrypt file
encrypt(key, inputFile, encryptedFile);
System.out.println("File encrypted successfully!");
// Decrypt file
decrypt(key, encryptedFile, decryptedFile);
System.out.println("File decrypted successfully!");
} catch (Exception e) {
e.printStackTrace();
}
}
}
In this code, the doCrypto() method uses the Rijndael algorithm to encrypt or decrypt the input file. The encrypt() and decrypt() methods use this method to perform the respective operations. The main() method shows an example of how to use these methods to encrypt and decrypt a file.
Note that in a real-world application, you would want to use a more secure method to generate the key, such as a key derivation function, and possibly also add some additional security features like authentication and integrity checks.
Applications of the Rijndael Algorithm
The Rijndael algorithm has many applications in modern cryptography due to its strength, efficiency, and flexibility. Some of the applications of the Rijndael algorithm are:
Data Encryption: Rijndael is widely used in data encryption applications, such as protecting sensitive information on computer systems, secure communication channels, and digital media.
File Transfer: Rijndael is often used to encrypt files during transmission over the internet, such as FTP or cloud-based file-sharing systems.
Wireless Communication: Rijndael can be used to secure wireless communication networks, such as WiFi, Bluetooth, and RFID.
Virtual Private Networks (VPNs): Rijndael is often used in VPNs to ensure secure communication between remote networks.
Electronic Payment Systems: Rijndael is used in various electronic payment systems, such as digital wallets, online banking, and e-commerce transactions.
Digital Rights Management (DRM): Rijndael is used in DRM systems to protect copyrighted content, such as music, movies, and books.
Military Communications: Rijndael is used to secure sensitive military communications and to protect classified information.
Overall, the Rijndael algorithm is a versatile and powerful tool for securing a wide range of applications that require confidentiality, integrity, and authentication.
.......and that's the end of the article. I was trying to learn about how encryption works in messaging apps and I came across the Rijndael Algorithm. I was amazed when I went deeper into the workings of the algorithm and tried to understand each step involved in it and how it became the Advanced Encryption Standard.
References:
